Healthcare Cybersecurity: The Biggest Stats and Trends in 2023
Tom has covered numerous cybersecurity topics whilst working as a writer. Based in the United Kingdom, Tom enjoys cooking and going on country walks in his free time.
Recent years have seen the healthcare sector become the primary focus of cybersecurity threats, contributing to an alarming 70% of all large-scale data security incidents. In this article, we’ll assess the state of healthcare cybersecurity in 2023, along with some of the biggest cybersecurity threats that target the industry.
Organizations in healthcare retain some of our most sensitive data, and often have glaring cybersecurity vulnerabilities, making it an obvious target for cyberattacks. Over the last two years, 45% of healthcare organizations experienced a data breach. We’ll cover some general stats on the issue, along with cybersecurity risks, impacts, and the steps healthcare companies can take to safeguard against cybersecurity incidents.
General Stats About Healthcare Cybersecurity
We’ll start things off with a few general stats, so you can get a feel for the state of data breaches, cyberattacks, and cybersecurity in the healthcare sector.
High-Profile Incidents
There have been several high-profile cyberattacks in the healthcare industry. Although healthcare cyberattacks may not always be on the same scale as other industries (such as the Marriott International breach that affected 500 million customers), the sensitive nature of work in the healthcare industry means cyberattacks can be much more damaging.
Given the treasure trove of personal information that can be found on the servers of hospitals and healthcare corporations, it’s unsurprising that hackers often target this data.
Patient data like names, addresses, contact details, and social security numbers can be stolen or held for ransom by hackers, while sensitive health data such as health insurance information and medical history can be used to target patients with scams and fraud.
In late December 2020, we published a report outlining a data breach in the Vietnamese medical company Innovative Solution for Healthcare (iSofH). The Safety Detectives cybersecurity team, led by Anurag Sen, found iSofH’s server in open form, exposing 80,000 people.
Although that’s not an insignificant number by any means, healthcare data breaches can have a much bigger impact, affecting millions of people at a time. One look at the top 10 healthcare data breaches of all time demonstrates the sheer size of some healthcare leaks.
| Top 10 Healthcare Data Breaches of All Time | |||
| Rank | Company | Date | No. of People Affected |
| 1. | Anthem Blue Cross | January 2015 | 78.8 Million |
| 2. | American Medical Collection Agency | March 2019 | 26.1 Million |
| 3. | Brazil Ministry of Health | November 2020 | 16+ Million |
| 4. | Premera Blue Cross | January 2015 | 11+ Million |
| 5. | Excellus BlueCross BlueShield | September 2015 | 10+ Million |
| 6. | Managed Care of North America | March 2023 | 8.9 Million |
| 7. | UK National Health Service (NHS) | July 2011 | 8.6 Million |
| 8. | PharMerica | March 2023 | 5.8 Million |
| 9. | MedicareSupplement.com | May 2019 | 5 Million |
| 10. | TRICARE | September 2011 | 4.9 Million |
The largest healthcare breach by far involves Anthem Blue Cross, an American health insurance company and the largest company in the Blue Cross Blue Shield Association.
The Anthem cyberattack affected a staggering 78.8 million people. Most of the victims affected in the breach were health plan members, though some non-members also had their personal details leaked.
The breach was caused by a phishing attack. On February 18th, an Anthem employee opened a phishing email that infected the user’s computer with malicious files. This allowed the hacker to gain access to 90 different systems within the company, escalating their privileges, and eventually reaching Anthem’s data warehouse.
An investigation carried out by the insurance commissioners’ examination team and security firm Mandiant outlines how names, social security numbers, medical ID numbers, addresses, dates of birth, emails, and employment details were all leaked during the breach.
The hacker is thought to be a “nation-state” hacker, acting on the behalf of a foreign government.
Since the breach, Anthem has invested heavily in cybersecurity measures, spending $260 million on consultants, security improvements, better systems of notification, and credit protection for impacted individuals.
Healthcare Cyber Attack Impact
From innocent customers to staff members and healthcare corporations, cyberattacks can have a huge impact on everyone involved.
These impacts can be broken down into 3 different types:
- Financial
- Organizational
- Personal
Financial Impact
Financially, cyberattacks cost companies a huge amount of money. A survey by HIMSS found that 17% of healthcare cybersecurity professionals claim that cyberattacks result in a monetary loss, such as wire fraud, ransom, or business email compromise.
Healthcare companies may also have to pay damages to affected individuals. If a company has handled customer data carelessly, data protection legislation could also enforce a hefty fine.
Organizational Impact
Cyberattacks can have an organizational impact on healthcare companies as well. Healthcare brands are built on the image of safety and protection. By putting customers at risk, healthcare companies can suffer reputational damage, decreasing trust among customers. And these companies know the risks — 50% of healthcare cybersecurity respondents are not confident of recovering from a cyber attack.
Cyberattacks can lead to a reduction in productivity, too. In a global survey regarding the healthcare industry, 26% of respondents said that cyber attacks disrupted IT operations, while 32% claimed that attacks disrupted the operation of the business. Ransom attacks and data leaks could force hospitals to close or prevent the use of medical technology. This leads to financial damages for the company and potential health impacts for patients.
Personal Impact
Healthcare cyberattacks can cause significant damage to people, their finances, and their physical and mental well-being. A hospital that closes its doors, or suffers a crippling reduction in productivity, may have to cancel appointments — leading to health impacts for patients.
Many healthcare data breach victims suffer medical identity theft, which costs patients an average of $13,500 to resolve. The stress associated with cybercrimes like identity theft, financial fraud, tax fraud, and other crimes related to a cyberattack, can have huge implications on the mental health of the victims.
Whose Data Is Leaked?
Overwhelmingly, the data leaked in healthcare data breaches belongs to patients, rather than other business entities or staff. Across all industries, public data containing personal information is exposed in 80% of data breaches — and the trend is no different in healthcare.
All of the largest healthcare data breaches involve patient data, with more than 175.1 million people affected overall. But this only represents a part of the total number of files leaked. While companies are required to disclose when their customers are affected by such breaches, they aren’t always forthcoming about the impact on other systems. This lack of full transparency makes it difficult to determine the full extent and implications of such breaches on business data.
Cyberattacks Are Damaging
In 2022, 49.6 million Americans were affected by healthcare data breaches. In fact, hacking ranks as one of the most damaging and impactful types of data breaches for healthcare payers and providers.
Costs
If online data breaches are so impactful, how does this impact translate into monetary damage?
With so much sensitive data at stake, healthcare data breaches are some of the most damaging leaks when compared to any other industry.
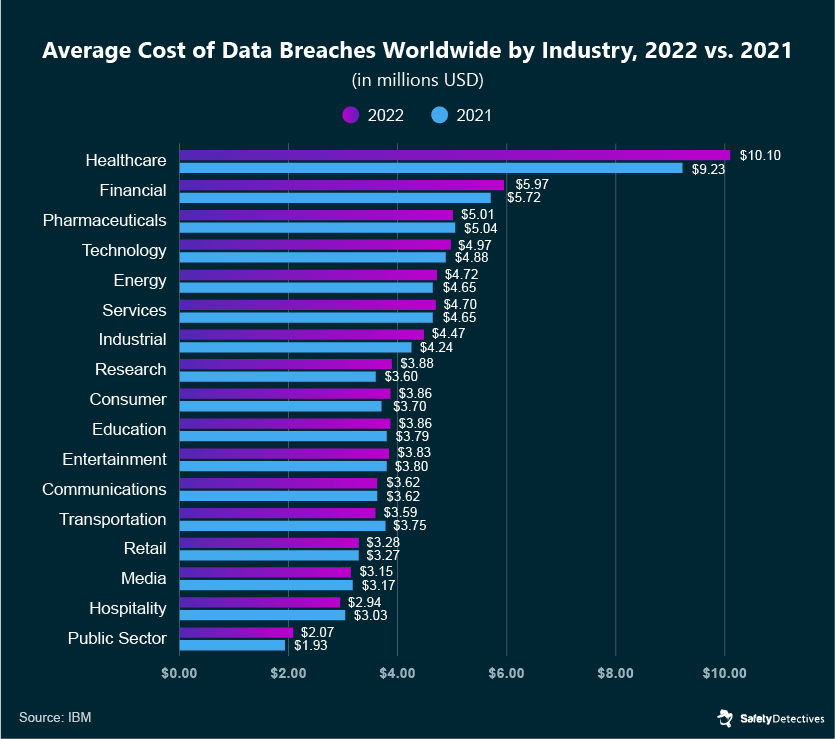
That’s right — a healthcare data breach costs a whopping $10.10 million on average. The healthcare industry is followed by the financial and pharmaceutical sectors, at $5.97m and $5.01m per data breach. However, I’m sure this is a table no one wants to be leading.
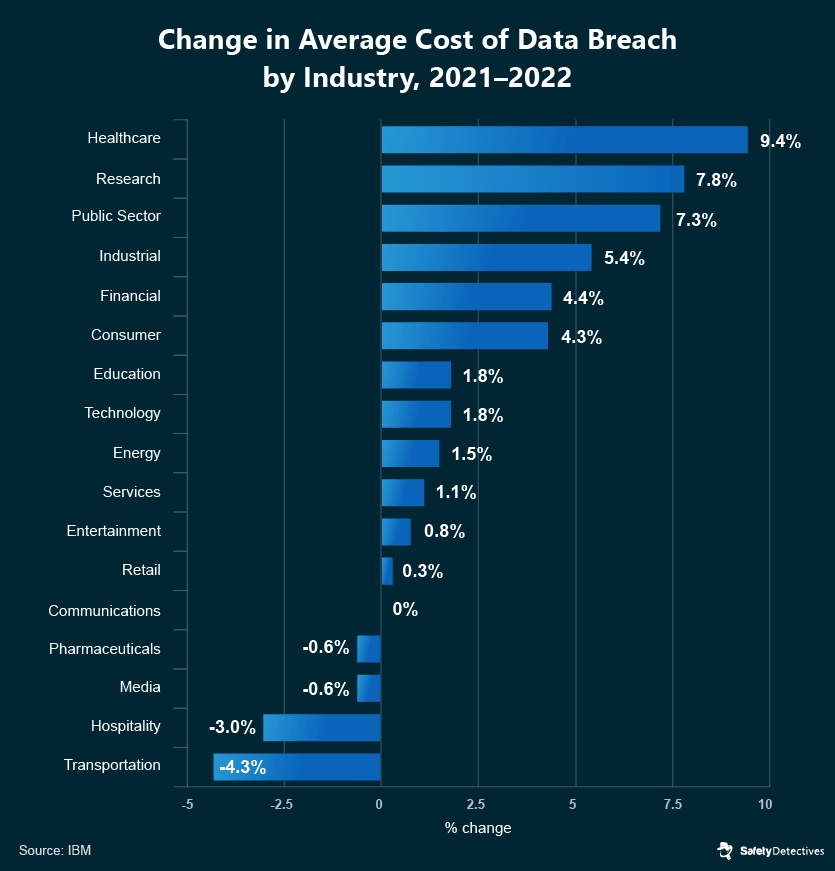
The cost of healthcare breaches used to be $9.23 million in 2021, but it rose by 9.4% in the span of a year. When compared to other industries, the latest data shows this was the highest increase in cost-per-breach in 2022, followed by the research industry’s 7.8% jump.
In addition to direct costs associated with a data breach, companies that have mishandled customer data could be under threat of government legislation and data protection laws. GDPR, for example, can fine companies as much as €20 million, or 4% of a company’s annual income.
Medical Data Is Valuable
Once a hacker has acquired a healthcare customer’s data, it can be sold for a large return on the dark web.
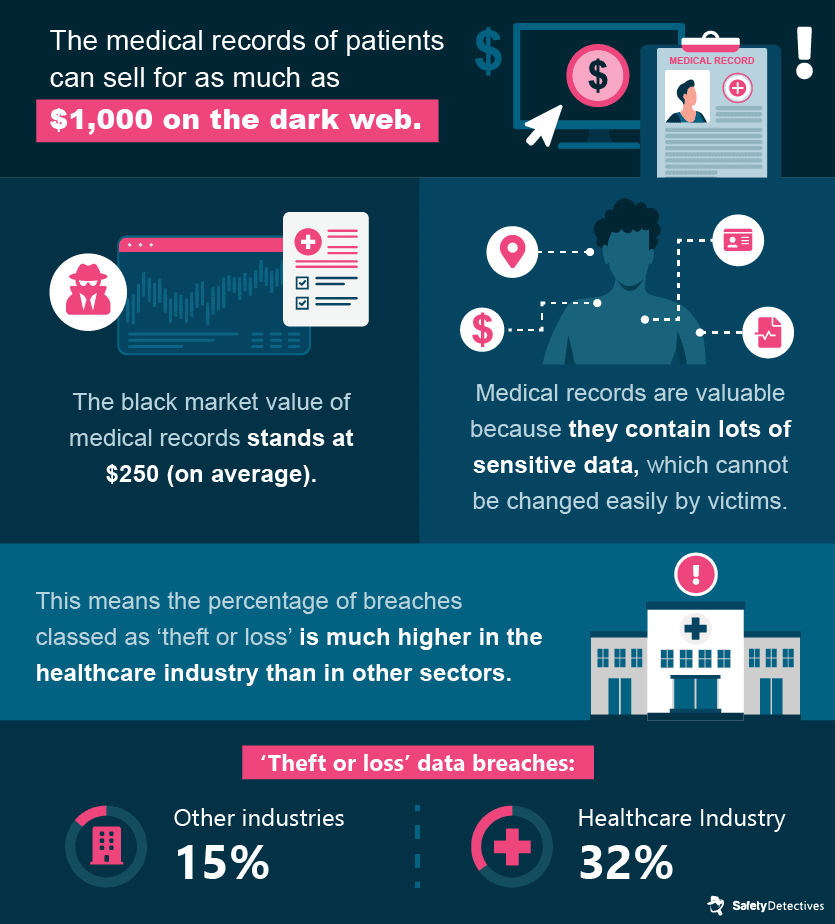
Medical records contain a bounty of unalterable personal details, like a person’s medical history, behavioral tendencies, demographics information, health insurance and social security number, contact information, and home address. While credit cards can be canceled, information on medical records is largely unchangeable and could lead to exposure to cybercrime for several years.
It’s for this reason that medical records are so valuable to hackers, and are targeted with such high frequency.
Cybersecurity Spend in Healthcare
The continued cyberattacks that have damaged healthcare companies and their customers have driven firms to invest more resources into security.
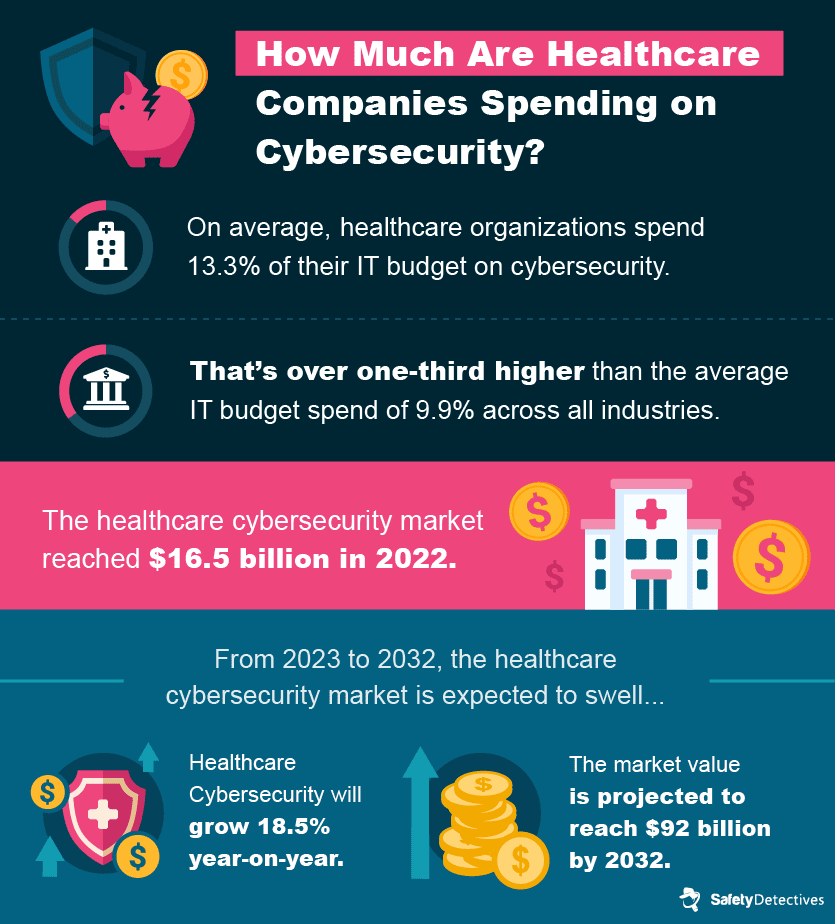
This trend is expected to continue in part due to the expected growth of global healthcare, which could reach $18 trillion in 2040.
In 2021, a report from SecurityScorecard ranked various industries by their proficiency in cybersecurity. The healthcare industry ranked 9th relative to other industries. During this time, healthcare companies were often choosing to save costs rather than protect themselves from cyberattacks and, among other mistakes, often placed unqualified executives in charge of cybersecurity.
However, the healthcare industry’s cybersecurity spending has increased since to match the growing complexity and frequency of attacks being leveraged against healthcare companies. It’s a cyber-arms race, and only time will tell how effective the industry’s new measures will be.
Cybersecurity Rating by Nation
So, which countries are best placed to deal with cybersecurity incidents in healthcare?
With healthcare being one of the most targeted sectors across the world, a quick look at cybersecurity ratings should tell us which countries are most at risk. The national cybersecurity index measures a nation’s cybersecurity level, preparedness for cyberattacks, and response to cyber incidents.
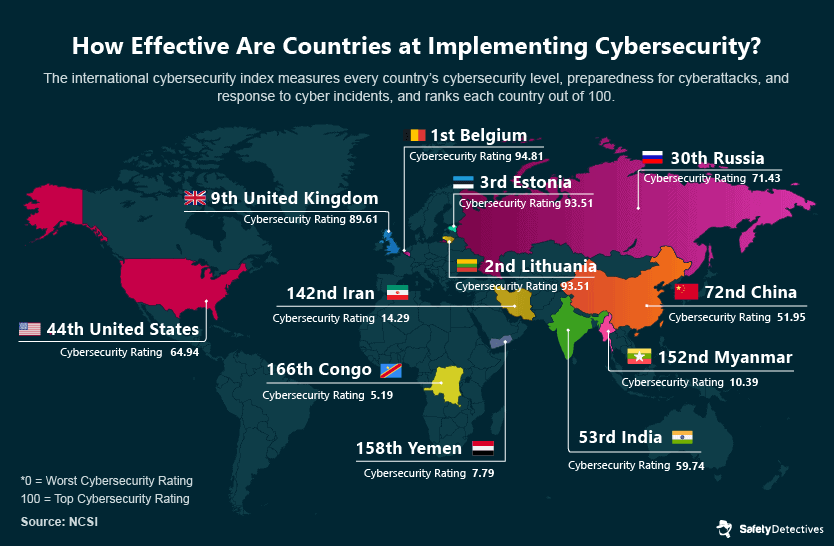
The severity of cyberattacks becomes even more evident when considering the case of Costa Rica, which ranks 77th on the National Cyber Security Index. The entire country was targeted, leading to the disruption of essential services, including healthcare and revenue collection. The attack paralyzed Costa Rica’s public health service by shutting down its computer systems.
The hackers demanded a ransom of $5 million in Bitcoin to unlock the infected servers, a demand to which the government firmly refused to yield, labeling the culprits as ‘terrorist groups.’ Consequently, the effects of the attack persisted for several months as the servers remained locked. Costa Rica received assistance from Microsoft and various governments in a collaborative effort to restore their services.
The United Kingdom’s National Health System (NHS) has also fallen victim to cyber threats. In 2022, the NHS was targeted by phishing campaigns, with over a thousand phishing messages originating from NHS IP addresses. These messages were sent from compromised email accounts belonging to 139 employees in England and Scotland. The United Kingdom ranks 9th on the National Cyber Security Index, yet it still needs to implement robust cybersecurity measures within the global healthcare sector.
Cyberattacks Are Getting Worse
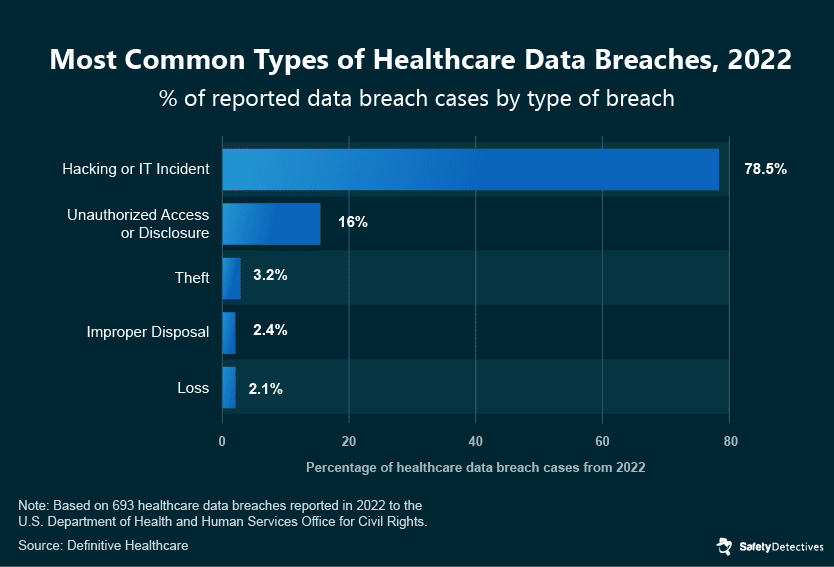
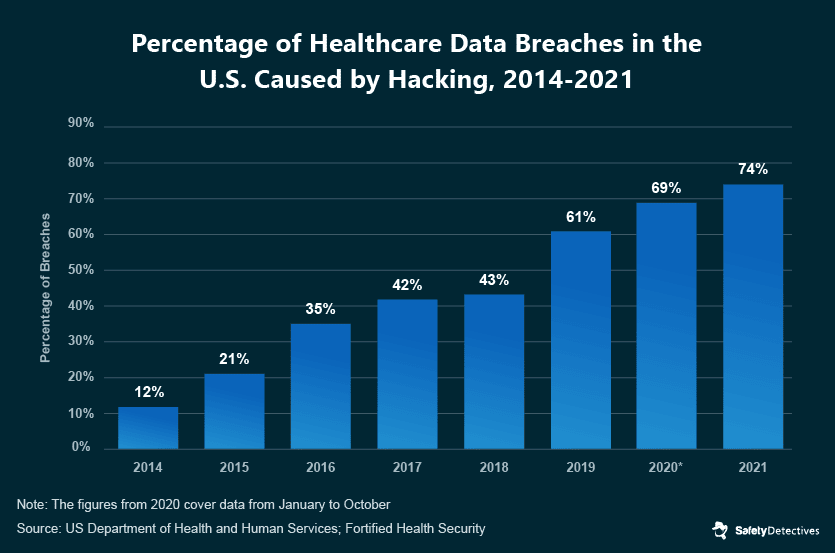
Over the past years, cyberattacks on healthcare institutions have been increasing both in frequency and severity, leading to more significant financial losses and compromising vast amounts of patient data. In 2022, for instance, 78% of healthcare data breaches resulted from hacking or IT incidents — a considerable leap from the 45% reported in 2018.
This upward trend, evidenced in HIPAA data, shows an alarming rise in exposed records over the years, with the exception of an anomalous spike in 2015 caused by Anthem’s breach. Since then, the number of exposed healthcare records has steadily increased compared to a decade ago, pointing to the escalating cybersecurity threat.
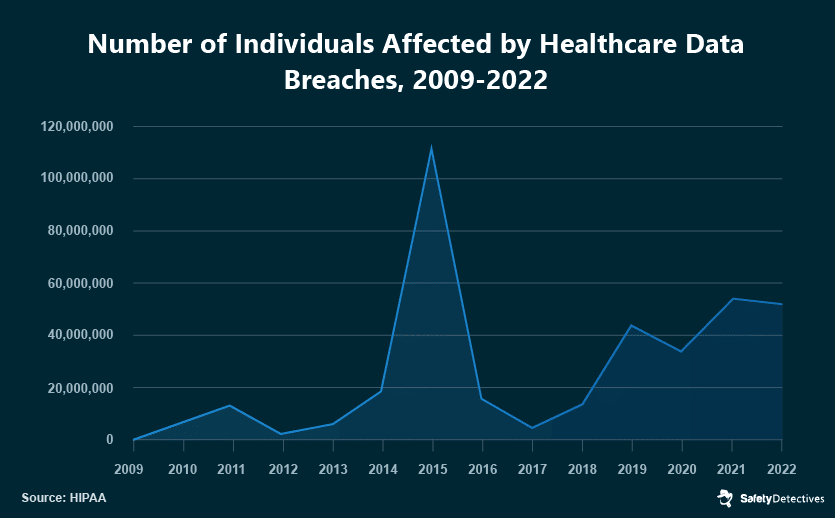
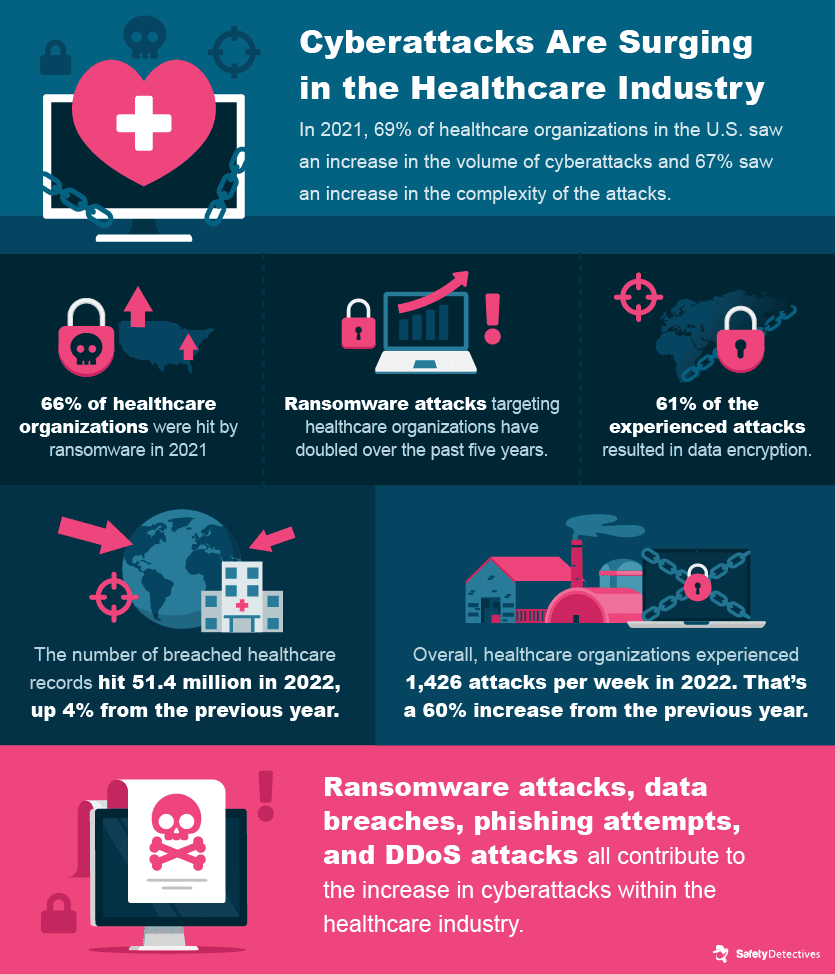
The challenges healthcare providers face today are numerous. The COVID-19 pandemic led to a diversion of resources from cybersecurity to immediate patient care. Then, in the late 2020 and early 2021 period, the existing vulnerabilities in healthcare cybersecurity systems became hard to ignore. This led to healthcare providers bearing the brunt of the highest number of cyberattacks globally in 2022.
Existing vulnerabilities, combined with the rapid transformation and technological advancements in healthcare, have made organizations in this sector attractive targets for cybercriminals.
The inadequate protection of medical devices, insufficient training of professionals in cybersecurity risks, frequent complex data exchanges, reliance on outdated IT systems, and a lack of unified data protection measures all contribute to this heightened vulnerability.
Robust cybersecurity in healthcare is a complex task, primarily because the professionals working in this industry often represent the weakest link in IT systems. Their primary focus is on medical practice and patient care, sometimes at the cost of vital aspects of health IT safety and privacy.
Cybersecurity Risks in the Healthcare Industry
We’ve covered the latest trends in healthcare cybersecurity for 2023. To know the issue inside and out, we must have an understanding of all the risks that healthcare providers are facing.
How Much Is Healthcare Targeted?
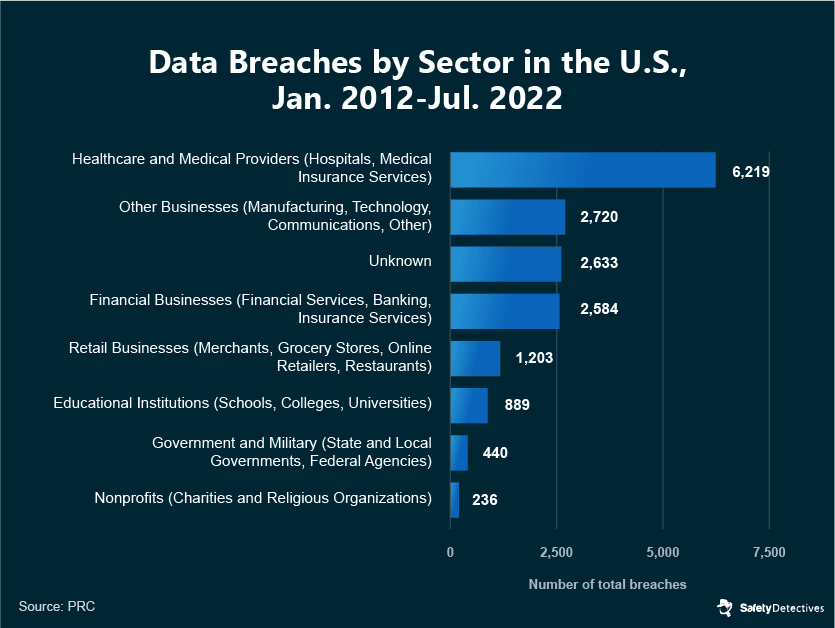
The healthcare sector remains a primary focus for cyberattacks. In 2022, a staggering 70% of all recorded data breaches pertained to this industry. Furthermore, a historical overview of the past decade reveals that healthcare data breaches have comprised approximately 37% of all such violations in the United States.
Highest Risks
In 2021, hacking was responsible for 74% of all healthcare breaches in the United States.
Hackers looking to steal data or carry out ransomware, DDoS, or any other type of cyber attack, will exploit certain vulnerabilities to gain access to a hospital’s systems and carry out malicious crimes.
Wandera, a company that provides businesses with cloud security solutions, published findings from months of research. Wandera’s report evaluated data on tens of thousands of users in a vast global database of healthcare organizations. The report’s findings demonstrate the different ways in which hackers are launching their attacks, by the percentage of organizations affected.
| High-Risk Entry Points for Hackers in the Healthcare Industry | |
| Threats | Healthcare Organizations Affected |
| Malicious network traffic | 72% |
| Phishing | 56% |
| Vulnerable OS (high risk) | 48% |
| Man-in-the-middle attack | 16% |
| Malware | 8% |
Wandera’s research outlines two different types of man-in-the-middle attacks as particularly troublesome.
- SSL stripping — Where an intermediate server disguises itself as a legitimate service.
- Targeted certificate spoof — Where an intermediate server poses as a genuine service.
What Are Each of These Risks?
- Malicious network traffic refers to any attack that begins with network access from an app or web service. This traffic can carry out malicious behavior such as downloading unauthorized software onto a healthcare computer or device. From there, hackers can gather information or disrupt the function of hospitals/devices.
- Phishing refers to any attempt to deceive users by convincing them to click a link, follow a web form, or submit sensitive personal data. If a user bites on a phishing attempt, hackers could gain access to a hospital’s system.
- Hackers could also target any Vulnerable OS (operating system) that is used within a healthcare organization. Older devices, or devices using older software, are not as secure against the threat of hackers when compared to newer devices. Some medical devices are also not designed with cybersecurity in mind.
- Man-in-the-middle attacks occur when a device has been manipulated to completely trust an unauthorized third party (i.e. a hacker). From there, a cyberattacker can transition through hospital systems, and gain access to information.
- Malware is an application or software that is created to cause harm or gain unauthorized access to a mobile device or system.
Prevalence of Specific Threat Vectors
While phishing, email compromise, and the exploitation of app misconfigurations are common points of entry for hackers, ransomware accounts for a significant portion of all cyber attacks. For data breaches alone, Tenable researchers found that ransomware was the primary threat in 35% of all data-related attacks.
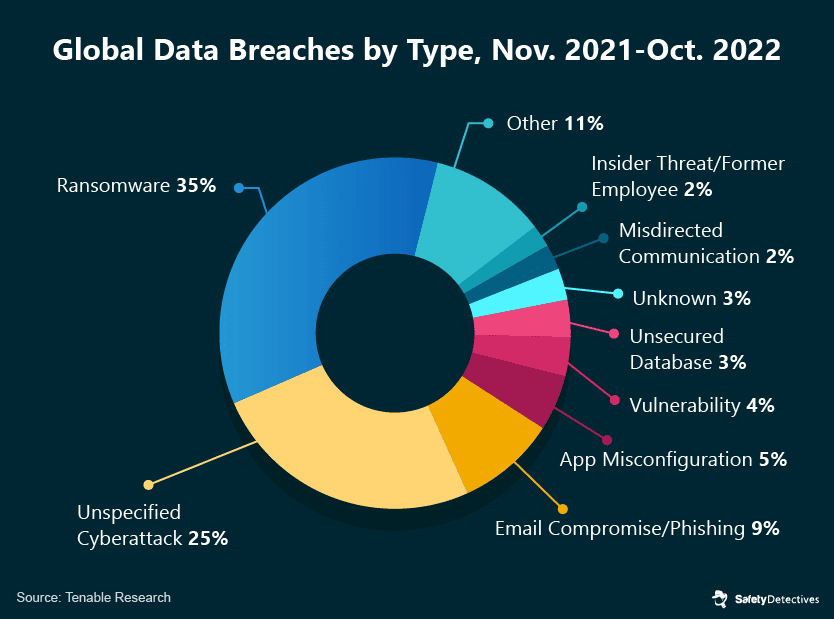
Ransomware is a form of malware that holds stolen data behind a paywall, with the threat of publication should an organization choose not to pay the ransom. Statistics suggest that around 61% of healthcare organizations pay a ransom to retrieve stolen data.
Cyberattackers using ransomware gain access to healthcare servers primarily through exploiting two different vulnerabilities in Virtual Private Networks (VPNs): the CVE-2019-19781 vulnerability and the CVE-2019-11510 vulnerability.
Elsewhere, hackers can also capture hospital systems using DDoS attacks. “Distributed denial-of-service” attacks target weak operating systems or old devices. They attempt to render a device or network resource unusable by taking control of it and disrupting the host device’s services.
DDoS attacks can result in the operations of a hospital shutting down, and hackers can hold hospitals to ransom before returning networks to working order. In 2022, there was a 150% increase in DDoS attacks worldwide compared to the previous year. These attacks affected various industries, with healthcare being the third most targeted sector, accounting for 11% of attack activity, preceded by technology (20%) and finance (53%).
Common Cybercrimes
Criminals can carry out all manner of fraudulent and criminal activities with sensitive personal data.
One of the most common crimes victims can experience is long-term identity theft and fraud. Over 70% of healthcare data breaches involve sensitive demographic or financial information that can be used to conduct crimes to this effect. By adopting the victim’s identity, criminals can open credit card accounts and loans in the victim’s name and take the money for themselves. Tax fraud and home equity fraud are two more avenues criminals may choose to take.
Criminals can also leverage details about a patient’s disease or terminal illness to conduct scams specific to their condition. This could include selling a miracle “at-home cure,” which is particularly cruel.
There is the issue of medical identity theft and fraud, too. With medical records, a criminal could obtain prescription medications, file fraudulent medical and insurance claims, and access certain medical services for free. It’s estimated that, in the U.S. alone, Medicare and Medicaid fraud cost over $100 billion every year.
Medical devices are also at the mercy of criminals. Hackers can take control of medical devices, disable them, and demand payment to restore them to working order. Healthcare providers must pay the ransom or risk patients dying without adequate healthcare support.
Medical devices are not designed to deal with the modern threat that hackers present. Criminals can use these devices to gain access to other servers, where they can get to sensitive personal data.
IoT devices — which are prevalent in medical settings — are also vulnerable to cyberattacks. We talk about these in-depth further down the page.
High profile ransomware attacks on medical devices and systems include:
- WannaCry, which affected institutions in 150 countries and brought the UK’s National Health Service (NHS) to a standstill. The severity of the situation led to the NHS refusing patients critical Accident & Emergency services.
- SamSam ransomware, which effectively held U.S. hospital records hostage behind a digital paywall. One hospital paid $55,000 to retrieve the data.
- Orangeworm, which targeted several different health institutions across the world, gaining unauthorized access to equipment and systems. This infiltration was, in all likelihood, aimed at carrying out covert espionage.
Popular Scams
Once a hacker or criminal has acquired a patient’s contact details, a few different scams are common within the healthcare industry.
One way in which scammers will attempt to con victims is through the offer of health and medical products. They could target victims based on their medical history. Generally, medical product scams are split into two categories: fake online pharmacies and miracle cures.
In a fake online pharmacy scam, the criminal will trick victims into paying for medical products. Of course, the offer is not from a legitimate pharmaceutical company. Customers will either receive bogus medications that do not work or nothing at all.
These scammers may even have a website that looks the part, and cheap prices without the need for a prescription that will seem too good to be true — because they are!
Miracle cure scams will offer quick, easy, and effective medications that provide hope to people with serious or chronic health conditions. These scams prey on vulnerable people in desperate situations. Miracle cure scams could offer treatments for anything from AIDS, cancer, or dementia, to arthritis or the common cold. They may even claim that their product cures all ailments, which is not possible. Scammers can charge huge sums for these specialized treatments, only for victims to find out they are not legitimate.
Risk Data in Healthcare
As we have already established, the kind of data stored in hospitals is sensitive. That’s why it’s so valuable to cybercriminals.
An extensive list of sensitive personal data is stored on medical records, from patient phone numbers to unalterable details like social security numbers.
But there are big risks involved for the healthcare institutions, too. Breaches can cripple the operations of a healthcare institution. 61% of healthcare cybersecurity respondents said that cybersecurity incidents disrupted non-emergency clinical care, while 28% believe emergency services were negatively affected. Furthermore, 17% of respondents believe a breach led to serious patient harm — and there can be legal implications whenever medical negligence is a concern.
Financial records, data on business operations, and valuable research into treatments or new technologies may also be stored on a healthcare organization’s database. Through accessing these files, hackers can conduct “corporate espionage,” gathering data on the business operations of a company. For example, cancer treatments in China have undercut the US market in recent years, and many people attribute this to the abundance of Chinese nation-state hackers involved in big data breaches.
One Frost Radar report highlights how hacks on financial records and revenue management systems can rack up heavy costs for healthcare organizations — with low insurance compensation and a reduced patient footprint.
Risk of IoT in Healthcare
When the IoT (or “Internet of Things”) is applied to medical science, it allows hospitals to monitor a patient’s care and health data in real-time. The technology is potentially groundbreaking, as it can help healthcare organizations provide a better quality of service for patients.
Doctors have the data they need at their fingertips, making it easier to know exactly why treatment is not working. For example, if a patient with a memory issue is not taking their tablets, tablets with an edible tracking chip inserted could let the doctor know.
IoT’s effectiveness has led to its widespread use throughout healthcare organizations. Approximately 60% of healthcare providers across the planet have incorporated IoT into their facilities, with the medical IoT market set to reach $312.7 billion worldwide by 2030.
However, opportunistic cybercriminals are now beginning to realize that IoT devices are particularly vulnerable. These devices are connected to the internet, and they provide a link to medical records and sensitive data. What’s more, IoT devices are relatively unprotected against hackers, all of which makes IoT a worthwhile target for cyberattacks.
If an IoT device uploads its data to a cloud-based database, something as simple as a poorly configured security patch could be the cue for hackers to conduct their attacks. Using the IoT device as an entry point, they could access the database and expose all of the files.
Internet-connected medical devices, including insulin pumps, intracardiac defibrillators, mobile cardiac telemetry, pacemakers, and intrathecal pain pumps, are notably prone to cyberattacks. In an assessment of more than 300 hospitals, researchers found that 53% of these devices had critical vulnerabilities. Alarmingly, it was discovered that 73% of IV pumps could potentially compromise patient safety due to their vulnerabilities.
Overall, IoT has a negative impact on the total cost of a data breach.
The Impact of the COVID-19 Pandemic on Cybercrime
The COVID-19 pandemic led to a substantial increase in cybercrime, with cyberattacks nearly doubling in 2020 compared to the previous year. The first month of lockdown in the United Kingdom witnessed a 400% increase in scams, highlighting the severity of the situation.
In September 2020, the Hospital of Düsseldorf University experienced a deadly cyber attack. Cybercriminals deployed ransomware, compromising the hospital’s servers and causing significant disruptions. Surgeries, medical examinations, and chemotherapies were postponed, while emergency patients had to be redirected. Tragically, a female patient sent to a hospital 35 km away died due to the delayed treatment.
Verizon reported a 58% rise in confirmed data breaches within the healthcare sector during 2020. The critical nature of medical data, especially during a pandemic, has made healthcare institutions an appealing target for cybercriminals.
Why the Pandemic Caused More Hacks
The healthcare industry, already stretched thin by the COVID-19 pandemic, found its focus redirected from cybersecurity to patient care. Consequently, this shift made healthcare institutions prime targets for cybercriminals who exploited these vulnerabilities, sometimes by seizing control of critical medical data. The importance of such data, especially during a pandemic, meant healthcare facilities were often compelled to pay substantial ransoms for data retrieval.
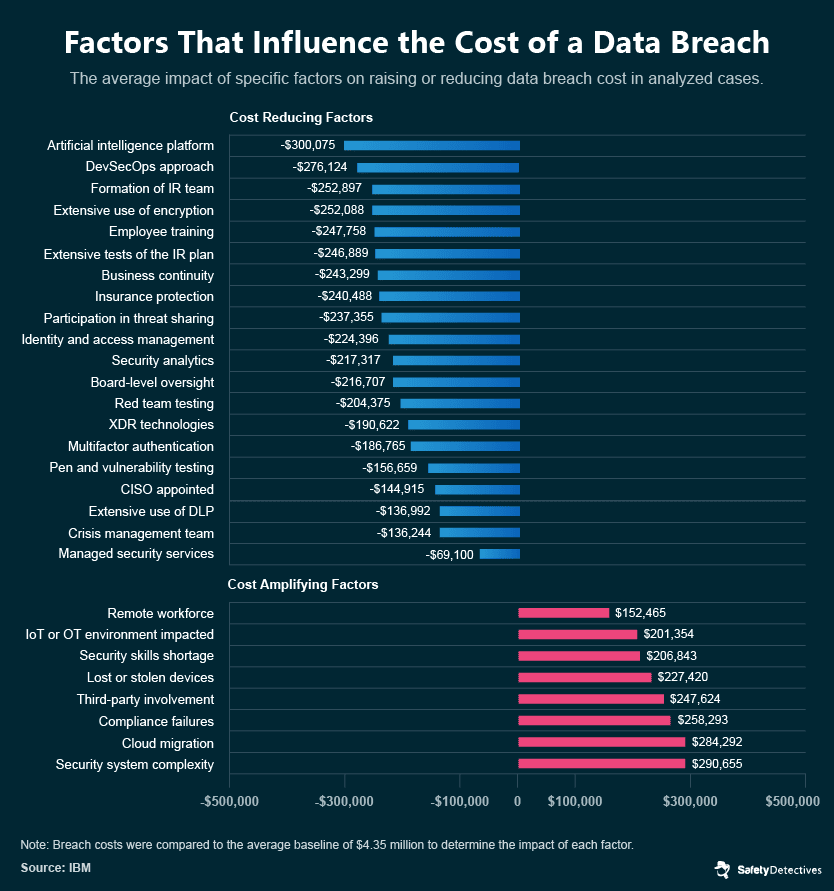
The shift to remote work further exacerbated these cybersecurity issues, presenting new opportunities for hackers through phishing scams and compromised login credentials. IBM research indicates the average cost of a data breach has surged by $137,000 per incident due to remote work scenarios.
The reasons behind this increase include reduced team interconnectivity, heightened individual susceptibility to phishing scams — 47% of remote employees cited distraction as the reason they fell for such scams — and decreased efficiency of cybersecurity teams. The latter point is emphasized by the 76% of remote workers who believe that the time taken to respond to cyberattacks and breaches has increased due to remote working conditions.
This highlights the need for stronger and more adaptable cybersecurity measures.
Popular Cyber Crimes During the Pandemic
The pandemic, while fundamentally changing the landscape of global healthcare, also reshaped the cyber threat landscape. As organizations worldwide pivoted to accommodate the new realities, cybercriminals capitalized on the uncertainty, fear, and reliance on digital technologies.
During this period, several types of cybercrime grew in prevalence, leveraging the unique conditions of the pandemic. In the following sections, we delve into the most prevalent cybercrimes that surged during the pandemic, highlighting the scope of the challenge and emphasizing the critical need for robust cybersecurity measures.
COVID-19 Phishing Scams
Phishing scams targeting COVID-related information became increasingly widespread. These scams predominantly involved email phishing attacks, specifically targeting healthcare staff who were working from home. Subject lines related to test results or personal protective equipment (PPE) were used to deceive individuals into clicking malicious links.
In April 2020, Google reported blocking approximately 18 million malware and phishing emails associated with COVID-19.
Big Health Data Breaches
Cybercriminals targeted large health corporations to breach their systems and gain access to valuable data. The World Health Organization (WHO) saw double the amount of cyberattacks during the pandemic, resulting in the leak of 450 active email addresses and thousands of COVID-19 response team emails.
Vaccine research labs also faced heightened threats, as the value of research data related to COVID-19 vaccines attracted cybercriminals.
Tracked Logins
The shift to remote work opened other avenues for hackers to steal data and access sensitive information. Companies using video-conferencing tools like Zoom saw their streams hacked or login details monitored. Hackers exploited this opportunity to listen in on meetings and learn about the company’s operations. Employee portals and company websites were also tracked.
While larger drug companies have measures to counter these threats, smaller entities, such as university departments involved in vaccine research, have been more vulnerable to practices like ‘password spraying,’ where hackers pepper accounts with generic passwords until they eventually gain access.
COVID-19 Apps
COVID-19 apps, including track-and-trace or venue check-in systems, proved vulnerable to hackers due to hasty and often subpar development. These apps, holding sensitive patient data, were criticized for weak security, exemplified by GDPR’s public censure of the UK’s test-and-trace project.
High-profile breaches were reported worldwide. Approximately 85% of track-and-trace apps and 71% of healthcare and medical apps exhibited major vulnerabilities. In fact, 91% of apps failed cryptographic tests, making them easy targets for hackers who could steal data, control linked devices, or breach systems. These apps often lacked essential protection technologies such as code obfuscation, tampering detection, or white-box cryptography, which could have thwarted 83% of serious cybersecurity threats.
High-Profile COVID-19 Data Leaks
Pfizer Breach
Pfizer, a leading pharmaceutical company involved in COVID-19 vaccine research, experienced cyberattacks in December 2020. Hackers targeted the European Medicines Agency (EMA) and stole data related to Pfizer’s vaccine candidate. The breached data included regulatory submission files, such as Word documents, PDFs, email screenshots, PowerPoint presentations, and EMA peer reviews. While the breach caused concern, it did not significantly damage Pfizer.
Wales Patient Data Breach
In Wales, COVID-19 patient data for 18,000 residents were accidentally posted on a public-facing database instead of a secure internal server. The exposed data included initials, dates of birth, geographical residences, and gender details of COVID-19-positive patients. The breach lasted for 20 hours before being taken down. While the majority of affected individuals faced a low risk, 1,926 people living in nursing homes, assisted living, and other enclosed settings could have been identified based on the available information.
Brazil COVID-19 Data Breach
An employee from a hospital in Brazil uploaded to GitHub software a spreadsheet containing government usernames, passwords, and access keys that provided entry onto systems containing sensitive COVID-19 patient data. This resulted in the exposure of the personal details and health information of 16 million Brazilians, including the former Brazilian president, Jair Bolsonaro.
The compromised systems included E-SUS-VE, used to track mild COVID-19 cases, and Sivep-Gripe, which displayed data for hospitalized patients. The exposed information included patient addresses, IDs, healthcare records, medical histories, and medication plans. The data was discovered by a GitHub user and subsequently removed.
Germany’s COVID-19 Tracking App
Programmers discovered a vulnerability in Germany’s COVID-19 track-and-trace app. The app contained a remote code execution (RCE) vulnerability, specifically in the part that validated user-supplied information. The swiftly addressed remote code execution (RCE) vulnerability could have enabled large-scale malware attacks and, if undetected, could have resulted in catastrophic consequences despite no substantial data loss.
Cybersecurity Threats in the Post-COVID Era
The World Economic Forum (WEF) has recognized cybersecurity threats as one of the top risks facing the world, particularly in the post-COVID era. According to a January 2022 report by the WEF, there has been an alarming 400% surge in cyber attacks targeting major corporations, governments, and critical infrastructures, including healthcare organizations since March 2020.
The COVID-19 pandemic significantly influenced the escalation and sophistication of cybercrime, according to Europol’s Internet Organized Crime Threat Assessment. The pandemic fueled trends like ransomware, DDoS attacks, and phishing attempts exploiting social vulnerabilities. Advanced malware forms emerged, including mobile malware circumventing two-factor authentication. Online fraud surged with increased online shopping, and criminals continued exploiting legitimate services like VPNs and cryptocurrencies.
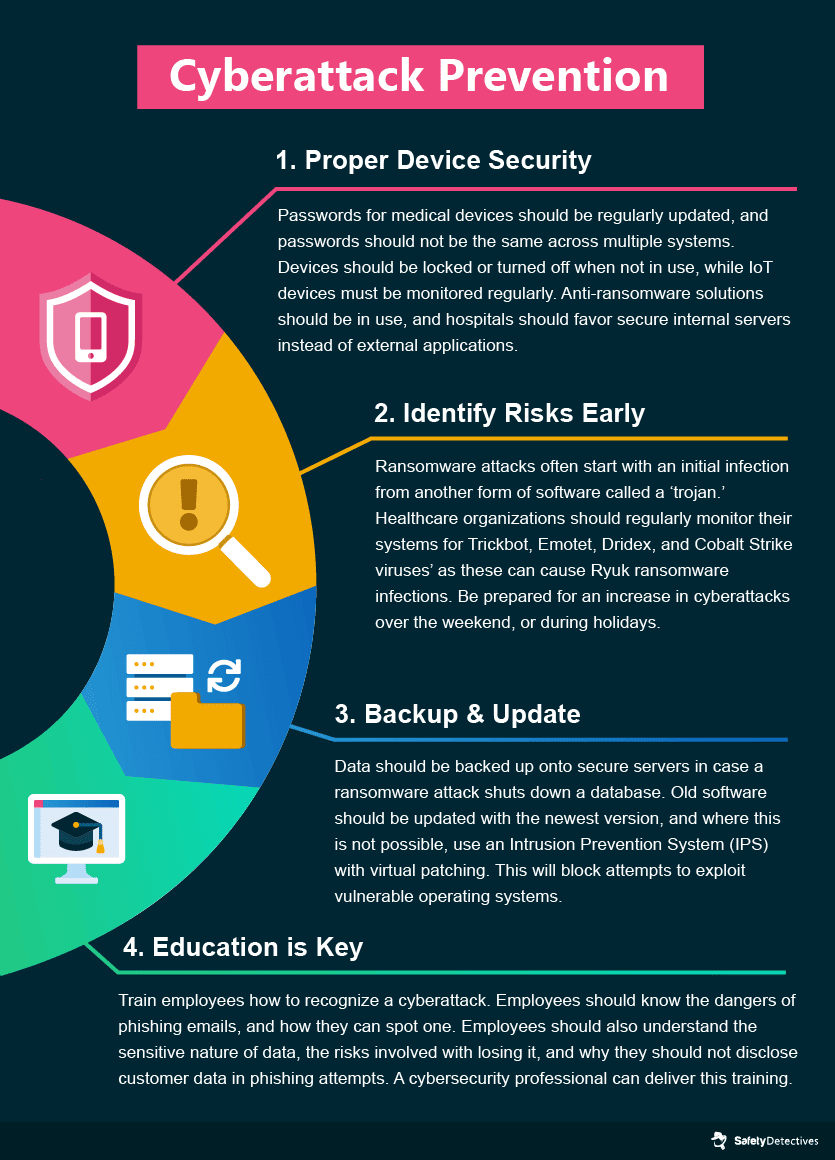
Tips to Prevent Ransomware and Phishing Attacks
After patient care, cybersecurity should be the highest priority for healthcare providers. Increasing the cybersecurity measures already in place leads to a reduction in the frequency of successful cyberattacks, along with a reduction in damages, both in terms of cost and the amount of data that is leaked. Organizations that fully deploy security automation save on average $3.05 million compared to companies that do not.
So, how do healthcare providers improve their cybersecurity?
Here are 4 key tips to safeguard from cyberattacks.
Final Thoughts
So there you have it — an extensive list of healthcare cybersecurity statistics covering everything you need to know on the topic.
These figures highlight the urgent need for robust cybersecurity measures and the importance of investing in the protection of sensitive medical data.
As technology advances and cyber threats evolve, healthcare organizations must prioritize cybersecurity as a fundamental aspect of their operations to safeguard patient information, ensure uninterrupted healthcare services, and ultimately ensure the well-being of individuals seeking medical care.
Share It:

SAFETYDETECTIVES CYBERSECURITY TEAMSafetyDetectives Cybersecurity TeamUPDATED ON: July 31, 2023
About the Author
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users